Disclosing a Data Breach to Pensoft
For no apparent reason, I stumbled upon a data breach of one of my accounts, password and all. It is a humbling lesson in how much trust we place in platforms to keep that information safe and secure.

In July, I got notified one of my passwords was available in a dark web data dump, alongside my email. I was able to pinpoint the breached service because I use unique passwords for each account. That service is Pensoft. If you have an account with Pensoft, I recommend you change your password and change wherever you might have reused it.
This blog is about discovering the leak, disclosing the breach to the service and the response that followed.
Discovering the leak
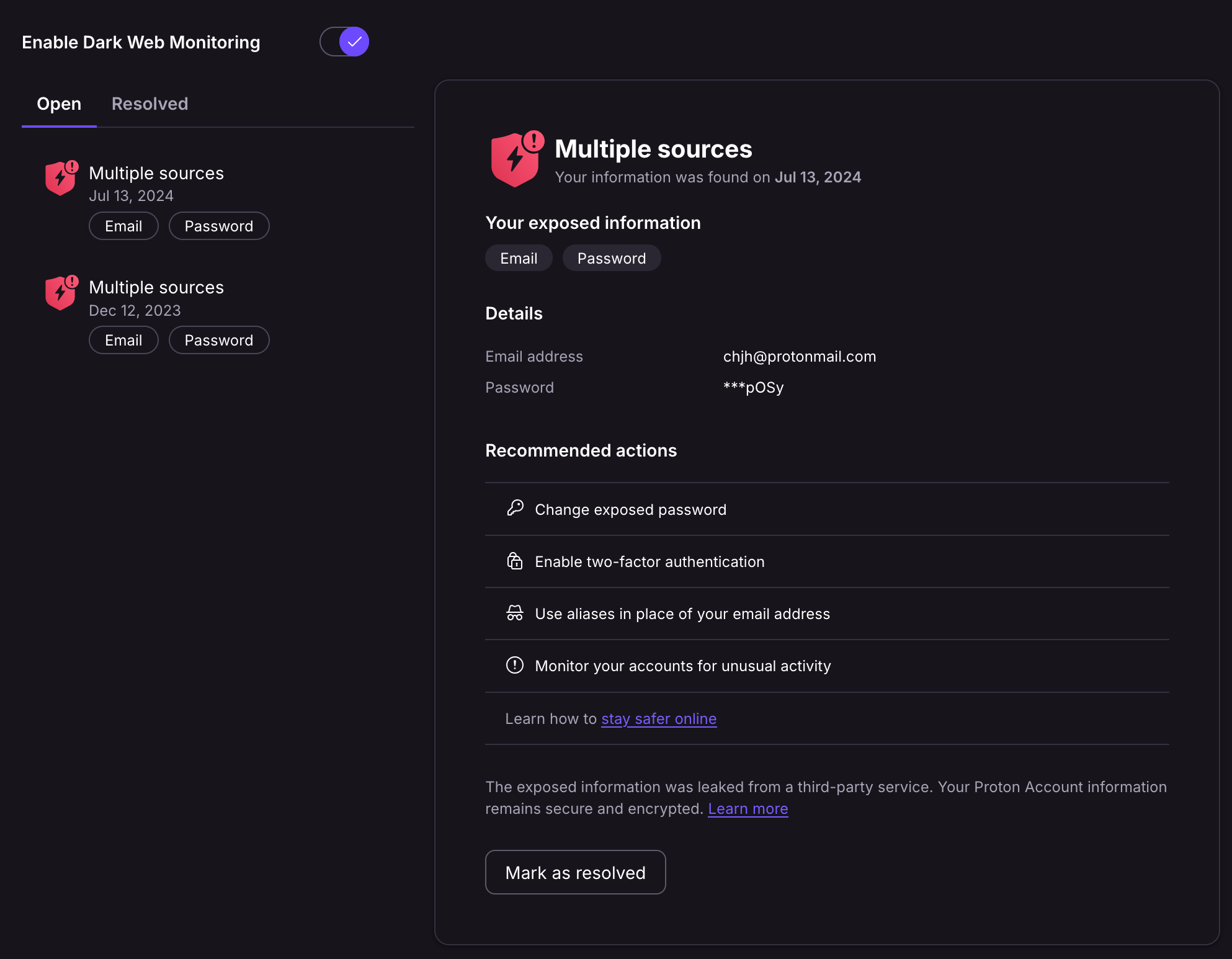
Up front: I do not spend time finding data breaches myself. It is too much work, I do not expect it to be rewarding, nor do I think I am the right person to do it. I just use Proton as my mail provider, and as a part of their services they provide their Pass Monitor. This includes so-called "dark web monitoring," which they describe as follows:
Proton’s dark web detection continuously scans dark web hubs associated with illicit activities, such as hacking forums and markets, searching databases for emails contained in data breaches.
I must admit I never thought much of this service. I even missed the original report that my password leaked – from December 2023! It was only in July, upon a second notification, that I noticed the leak and took it seriously because it displayed the final four characters of my actual password.
Disclosing the breach
At first, I did not believe I was the first to discover this breach. I checked the Pensoft Blog for any mention of breaches and found none. Additionally, under Recital 86 of the General Data Protection Regulation (GDPR), Pensoft is obligated to notify people with accounts that there was a (potential) leak of passwords. Given that I have an account, I would have received one – but I also could not find one in my emails.
I contacted Pensoft Executive Leadership on July 18th with the following email, to notify them of the breach:
It has come to my attention that my Pensoft credentials are exposed in a released data breach. I was not informed of this by Pensoft directly, so you may not be aware there was a data breach to begin with. I am bringing this to your attention so that you can investigate your servers for any such breaches and data exfiltration.
I was able to identify the data breach was at Pensoft because I use unique passwords for each service, and the exposed password matches my Pensoft.net account. I already reset it so access to my account is no longer possible.
I understand this is a sensitive matter, and I will hold off on making any public comments in your direction to ensure you have time to investigate and prepare your post-mortem. In case there is no substantive response on the matter in the next two weeks (either in this thread or directly as an account holder on your platform), I will share this data breach in the public interest. If in those two weeks, you share initial steps taken but that you need more time to do a proper investigation, please let me know and I can hold off for another two weeks before going public.
The longer user's passwords are exposed without response, the longer people's personal information are at risk, so I hope for a proportional response to this urgent matter.
Response to the disclosure
First off, Pensoft leadership was fast to reply. My disclosure was around 9AM and their response at around 2PM (my local time). There was some request for clarification as to how I determined there was a breach, which was similar to the clarification I give above. I did not receive any substantive response on the breach itself.
The most important responses from their side are the following quotes:
we are not aware of having a data breach.
This acknowledges they were not aware of any breach before my disclosing it on July 18th, 2024.
we already started a thorough check of the system. Based on the results of the check we will decide what will be the next steps.
I have not heard about the results of this check in response to the disclosure or as an account holder on the Pensoft platform.
What I surly know is that since ~7-8 years we did not store passwords in a clear text and since two years we are using salt when hashing.
This final quote reveals how the password may well have leaked. More than two years ago they stored passwords without salting and only used hashing. From a security perspective, this is horrible practice. Depending on what algorithm they used to hash the passwords, it is trivial or mildly inconvenient to brute force. Without salting, it is only a matter of time, not capability to crack them. This also means that it is likely this is how the original passwords were cracked and leaked.
It has been over two weeks since my initial disclosure of the breach, yet Pensoft has taken no substantive steps in response, except stating they would investigate for breaches. I received a private backchannel message from someone affiliated with Pensoft that they "do not see any hints that there was a leak."
Since my disclosure, there has been no official acknowledgment of this risk to their users. Because Pensoft is not making this disclosure to users, I am posting this blog. I am confident that Pensoft was breached sometime before December 2023. There is no other way the unique password I used for my Pensoft account leaked and was presented back to me as part of that dump.
My recommendation is: If you have an account on Pensoft, go reset your password. If you used the same password for other services, reset those as well. There is a risk your account can be accessed by bad actors in the meantime.




Comments ()